In the rapidly evolving pharmaceutical industry, computerized systems play a vital role in drug development, manufacturing, quality control, and regulatory compliance. As technology advances, ensuring the reliability, security, and compliance of these systems becomes increasingly important. This is where Computer Software Assurance (CSA), a new and modern concept for Computer System Validation (CSV), comes into play. In this blog post, we aim to answer the following questions:
- What is Computer Software Assurance?
- What are the key differences between CSA and CSV?
- What should be the first steps to transition from CSV to CSA in the Pharmaceutical Industry?
- Why adopt the CSA approach?
What is Computer Software Assurance (CSA)?
According to the FDA’s “Computer Software Assurance for Production and Quality System Software” guide, Computer Software Assurance (CSA) is a risk-based approach for establishing and maintaining confidence that software is fit for its intended use.
Its goal is to provide confidence in the proper functioning of software applications, databases, networks, and other components that make up a computerized system. This assurance is essential to mitigate risks, prevent system failures, protect sensitive data, and comply with regulatory requirements.
This FDA guide is currently in draft status, and its application is specifically for medical devices. However, it is important to say that ISPE is currently describing similar principles as part of their Good Practice guide on data integrity (ISPE GAMP® Guide: Records and Data Integrity, March 2017).
Following this risk-based approach makes companies focus on no more than the necessary validation workload to address the software risk. Traditional Computer System Validation (CSV) focuses a lot on documentation, which is not the purpose according to the key principle of the GAMP5 guide. Detailed scripted testing activities must cover every click and function of the system. The concept of Critical thinking is in this approach almost completely subdued by the pressure of Good Documentation Practices and strict validation testing activities.
In CSA on the other hand, critical thinking is key. This approach leads to a more commensurate amount of evidence and documentation. This allows to make efficient use of resources while at the same time encouraging product quality. In general, CSA focuses on:
- Leverage experienced SMEs, who apply critical thinking to determine test and documentation strategies in a risk-based approach.
- Generate supporting evidence only where it brings value to the quality of the testing.
- Spend more time actively testing to find defects and less time generating specifications in advance
Figure 1. CSV Approach & Figure 2. CSA Approach
In the context of Computer Software Assurance (CSA), it’s crucial that software used in production environments, as well as those integrated into quality systems, are rigorously managed throughout the entire validation lifecycle.
CSA aims to offer manufacturing companies a flexible and agile framework, enabling them to employ a range of principles and methodologies. These can include risk-based testing, unscripted testing, continuous performance monitoring, data oversight, and external validation activities, such as those conducted by software suppliers.
Moreover, CSA encourages organizations to take advantage of a variety of best practices, wherever applicable and beneficial:
- Utilizing activities and validations already completed by the software supplier to avoid redundancy.
- Implementing controls at strategically optimal points in the project timeline to effectively mitigate risks.
- Employing relevant and effective testing techniques consistently throughout the project.
- Leveraging specialized tools like bug trackers and comparison utilities to improve quality and efficiency.
- Adopting agile approaches that facilitate iterative specification and verification cycles, allowing for continuous improvement.
- Actively and continually monitoring both existing and emerging risks, while assessing the effectiveness of current risk mitigation strategies.
By adopting these guidelines, CSA seeks to ensure that software consistently maintains its validated state, thereby enhancing overall system reliability and integrity.
What are some key differences between Computer Software Assurance (CSA) and Computer System Validation (CSV)?
Technically speaking, both CSV and CSA have the same concept when it comes to delivering a high-quality product to the end users. However, there are slight differences between the two. Listed below are a few differences and how the CSA can be of an advantage:
1. Extensive evidence with little or no added value to the system quality
In scripted testing of CSV practitioners, it is a common misconception that extensive screenshots are required to provide objective evidence to demonstrate validation of computer systems used in the automation of business processes. CSA addresses this misconception by clarifying the purpose of the objective evidence and what constitutes an acceptable record.
2. Critical thinking, Risk Class, and Associated level of testing
In most cases, system requirements are classified but not to the level of the risk classification (RC). and critical business scenarios are not realized.
The involvement of experienced SMEs is crucial in the following areas:
- in identifying the risk class
- experienced-based input in realizing the test scenarios.
Risk class is an important attribute of a specification, as the level of the test effort is derived from this.
The higher the risk class, the greater attention must be given, and depending on critical business scenarios defined by the experienced SME, simple or complex tests can be performed. Low risk such as cosmetic requirements may not need to be tested intensively and rather fall under dynamic testing.
In the traditional way of validation, all requirements regardless of the risk class in scripted testing. Development of a test script:
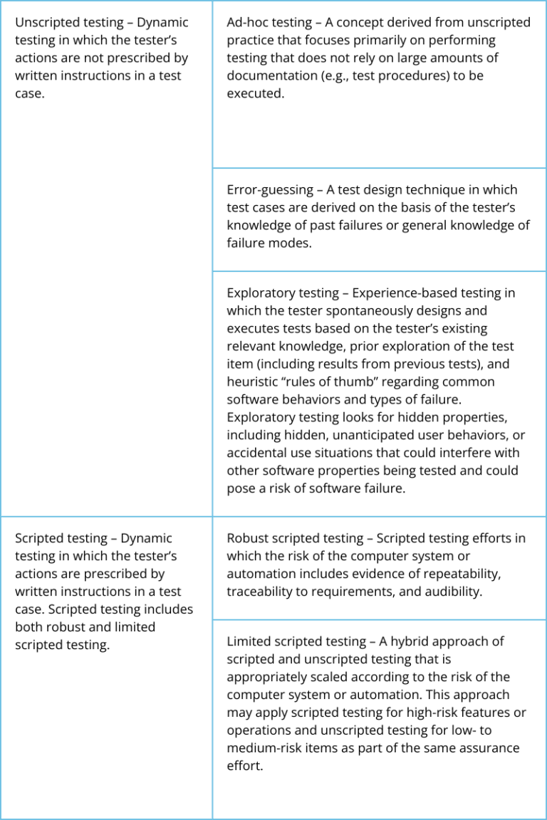
Table 1 – Unscripted and Scripted testing is further detailed in the table below.
3. COTs and leveraging of test effort with Supplier’s validation package.
Specifically for COT systems, most suppliers provide their own validation package. It is most likely that the test consists of all system functionality, as such you might need to filter out which test is relevant to the functionalities used by your organization. This is also highly recommended by the CSA approach.
4. Shorter timeline for deployment
With less burden and complex process, the CSA approach will help to optimize the use of resources, time, and effort without sacrificing the quality.
Computer Software Assurance in Pharmaceutical Industry: First steps
Here are some steps to perform Computer Software Assurance:
1. Define Scope and Objectives
Clearly define the scope of the computerized system that requires assurance. Identify the specific objectives you want to achieve through the assurance process. This could include regulatory compliance, system reliability, data integrity, and security.
2. Risk Assessment
Conduct a comprehensive risk assessment to identify potential risks and vulnerabilities associated with the computerized system. Consider both internal and external factors that could impact the system’s performance, such as software bugs, hardware failures, cyber threats, and regulatory requirements.
3. Develop Assurance Strategy
Based on the identified risks, develop a tailored assurance strategy. This strategy should outline the activities and controls necessary to address the identified risks effectively. It may include activities such as testing, validation, documentation review, audits, and security assessments.
4. Documentation review
Review the system documentation, including functional specifications, design documents, operating procedures, and change management processes. Ensure that the documentation accurately reflects the system’s configuration, functionality, and security controls. Identify any gaps or discrepancies that need to be addressed.
5. Testing and Validation
Perform testing and validation activities to ensure that the computerized system functions as intended. This may include unit testing, integration testing, system testing, and user acceptance testing and may also switch and include unscripted testing and the usage of tools as part of the testing activities. This is to verify that the system meets the specified requirements and operates correctly under normal and abnormal conditions.
6. Data Integrity and Security
Assess the system’s data integrity controls and security measures. Ensure that appropriate safeguards are in place to protect sensitive data from unauthorized access, modification, or loss. Evaluate encryption mechanisms, user access controls, audit trails, and disaster recovery processes.
7. Compliance Assessment
Determine if the computerized system complies with applicable regulatory requirements and industry standards. This may involve reviewing regulations such as FDA’s 21 CFR Part 11 for electronic records and signatures or ISO 27001 for information security management.
8. Audit and Review
Conduct periodic audits and reviews to assess the ongoing effectiveness of the computerized system’s controls. This helps to identify any deviations, weaknesses, or areas for improvement. Update the assurance strategy and controls based on the audit findings.
9. Documentation and Reporting
Document the assurance activities performed, findings, and recommendations. Create a detailed report summarizing the assurance process, including any identified risks, control measures, and their status. This report can be used for management review, compliance purposes, and as a reference for future assessments.
10. Continuous Improvement
Computerized Systems Assurance is an ongoing process. Continuously monitor the system’s performance, evaluate emerging risks, and update controls accordingly. Stay informed about technological advancements, regulatory changes, and industry best practices to ensure the system remains reliable and secure.
In conclusion, why should you adopt CSA?
Implementing Computer Software Assurance in the pharmaceutical industry is essential for ensuring the reliability, security, and compliance of computerized systems. By following the steps previously mentioned, pharmaceutical companies can lay a strong foundation for effective CSA implementation.
Remember, CSA is an ongoing process that requires collaboration, adaptability, and a commitment to staying ahead of regulatory requirements and technological advancements to safeguard the integrity of computerized systems and maintain patient safety.
In conjunction with your current CSV process, the CSA approach can help streamline your process. The benefits are as follows:
|







.png?width=109&height=108&name=Pharma%20(2).png)
.png?width=111&height=108&name=Medical%20Devices%20(2).png)
.png?width=84&height=107&name=IVD%20(2).png)














.jpg)







